- The North Korean-linked Lazarus Group has stolen at least $3.4 billion in crypto.
- Since first emerging in 2007, the group has carried out global attacks to fuel North Korea’s nuclear weapons programme.
- Here’s a timeline of every known Lazarus hack over 16 years.
As of 2023, cybercrime group Lazarus is estimated to have stolen at least $3.4 billion in cryptocurrencies since it appeared in 2007.
That figure is based on DL News’ calculations of hacks linked to the North Korean cybercrime gang.
Crypto exchange CoinEx is the latest to be hacked by the North Korean-linked organisation, after attackers took about $54 million on September 12.
“Lazarus Group has been one of the most persistent and effective threat actors in the cryptocurrency space,” Hugh Brooks, director of security operations at blockchain research firm CertiK, told DL News.
NOW READ: Top 10 crypto hacks of 2023 — Stake ranks fifth as hackers wipe $735m
DL News reported in April on a possible link between Lazarus and North Korea’s nuclear programme.
And the gang’s theft is not confined to crypto, he said. The group was behind the 2014 hack of Sony Pictures, and earlier Distributed Denial of Service, or DDoS, attacks against South Korean and US targets.
But since turning attention to the crypto and web3, Brooks said, “the group has magnified the impact of its efforts.”
In 2023, Lazarus has been blamed for at least $256 million in crypto stolen in hacks.
While that pales in comparison to last year’s estimated figure of $1.7 billion, it makes up around 30% of the $835 million stolen from crypto and DeFi projects in 2023, according to DefiLlama.
Here’s everything you need to know about the Lazarus Group.
Known Lazarus activities
2007
- March — Development of the first generation malware used in a number of later attacks attributed to Lazarus starts, according to a report by software company Novetta.
2009
- July 4 - Lazarus attacked websites in South Korea and the US, causing several dozen websites to go down. The attacks kicked off the beginning of what the group referred to as “Operation Troy,” a campaign of cybercrime. Researchers drew links between these cyberattacks with later attacks attributed to North Korea.
2012
- “Operation 1Mission,” a cybercrime campaign focused on South Korean targets, begins, according to Novetta’s research.
2013
- March 20 — Two groups, referring to themselves as NewRomantic Cyber Army Team and WhoIs Team, conduct cyberattacks on South Korean institutions, including broadcast companies, financial firms, and an internet service provider. The attacks were dubbed the “DarkSeoul wiper attacks,” as they wiped computer hard drives. The attacks caused widespread disruptions of ATM services in South Korea. Novetta and others attributed the attacks to Lazarus.
2014
- November — Lazarus, operating under the name Guardians of Peace, hacked Sony Pictures Entertainment in retaliation for the movie “The Interview,” a comedy that depicted an assassination attempt against North Korea’s leader. The hack was the first of many which would later be attributed to Lazarus by the US Department of Justice. Attackers leaked Sony employees’ emails and personal information, published on Wikileaks in 2015.
2016
- Led by Novetta, a consortium of researchers carried out “Operation Blockbuster,” which identified the source of the Sony Pictures hack as Lazarus. Novetta identified the toolset used by Lazarus, which would make future attribution easier for authorities.
- February — Attackers managed to illegally transfer close to $101 million in funds from Bangladesh Bank’s account at the Federal Reserve Bank of New York via the international Swift payments system. Lazarus initially sent 35 transaction requests that would have netted close to $1 billion if successful, but only five made it through. Security companies including Symantec and BAE Systems later attributed the hack to Lazarus.
2017
- April — Hackers stole $73 million from Bitcoin exchange Youbit, which contributed to its bankruptcy in December 2017. South Korean Internet and Security Agency KISA blamed Lazarus.
- May 12 — Lazarus carried out the WannaCry ransomware attack, which affected hundreds of thousands of computers globally. WannaCry used a ransom mechanism to force victims to pay to have their data restored. The US, UK, and several other countries later directly blamed North Korea for the attack, and asserted that Lazarus may have been the actor.
- December 7 — Attackers hit crypto cloud-mining marketplace Nicehash for over 4,500 Bitcoin, valued at over $60 million.
2018
- January 16 — Recorded Future released a report that linked Lazarus to the 2017 hacks. The report highlighted “continuation of North Korea’s interest in cryptocurrency” and highlighted its role in helping avoid sanctions.
- Group-IB reported that Lazarus stole $571 million worth of crypto in 2017 across five attacks.
2019
- March — CoinDesk attributed about $19 million to abnormal transactions carried out by Lazarus against Upbit exchange, citing security company East Security.
- September 13 — The Treasury Department sanctioned Lazarus, stating “state-sponsored hacking groups likely stole around $571 million” in crypto from five exchanges in Asia between January 2017 and September 2018, confirming prior reports.
2020
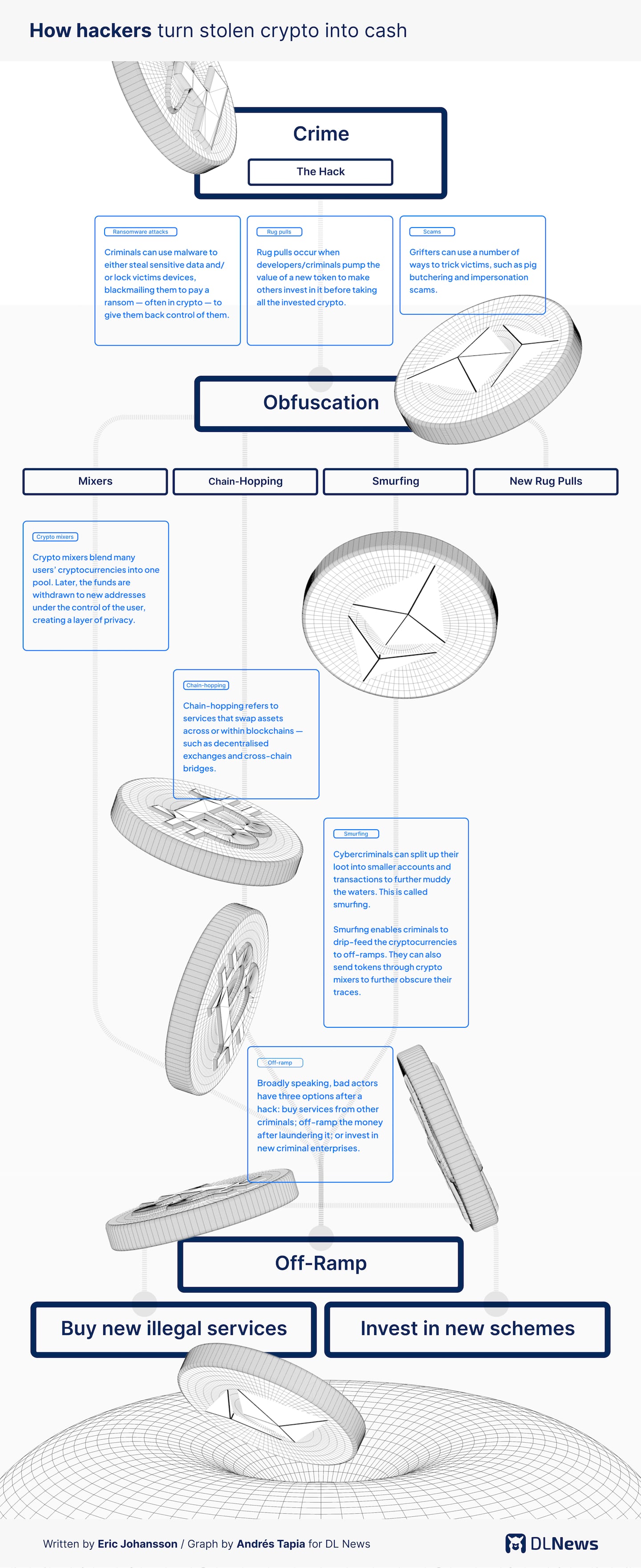
- January 21 — Chainalysis reported on 2019′s hacks, in which it outlined Lazarus’s adoption of more sophisticated phishing methods, as well as the increased use of crypto mixers like Tornado Cash. Tumblers are one of the many ways cybercriminals hide their tracks and cash out their stolen lot.
- March 2 — The US Department of the Treasury sanctioned two Chinese nationals, Tian Yinyin and Li Jiadong, for assisting the Lazarus group to launder funds retrieved in four hacks from 2017 to 2019. The DOJ said Yinyin and Jiadong altered photos to circumvent know-your-customer rules levied by trusted exchanges.
- October 27 — Lazarus hit Swedish pharmaceutical company AstraZeneca in a data breach amid the Covid-19 pandemic. Several similar attacks were carried out on vaccine makers throughout the year, but AstraZeneca was one directly attributed to Lazarus.
2021
- January — Hackers targeted cybersecurity researchers via social media such as Twitter, LinkedIn, and GitHub, according to research by Google’s Threat Analysis Team. The hackers posed as software researchers and convince targets to download malicious software — a tactic known as social engineering — to acquire vulnerable research data.
- February 9 — Chainalysis reported that Lazarus stole $275 million in crypto in 2020, more than half of funds hacked that year.
- February 17 — The US Department of Justice indicted Park Jin Hyok, Jon Chang Hyok, and Kim Il Park — all members of North Korea’s Reconnaissance General Bureau — for their alleged participation in Lazarus hacks.
2022
- January 14 — Chainalysis reported Lazarus stole $400 million in crypto in 2021.
- March 23 — At $625 million stolen, the Ronin Bridge exploit remains the biggest DeFi exploit ever and was attributed to Lazarus by the FBI. Ronin Bridge was built as a sidechain to allow users of popular web3 game Axie Infinity to bridge funds from other blockchains. The attackers carried out a spearfishing attack which enabled them to obtain the private keys necessary to drain the bridge. The attacker then routed the stolen funds through Tornado Cash, as well as several centralised exchanges, according to a report by CertiK.
- June 24 — Lazarus stole $99.6 million from blockchain Harmony’s “Horizon Bridge,” and laundered funds through Tornado Cash. Crypto investigators Elliptic traced the stolen funds, and was the first to attribute the hack to Lazarus. The FBI later acknowledged Elliptic’s findings.
- August 16 — Research firm ESET Research exposed an instance of a long-running Lazarus programme it called Operation In(ter)ception. Lazarus lured macOS users to fake job vacancies at crypto exchange Coinbase, which were malicious links. Researchers at SentinelOne tracked further spearfishing campaigns directed at Crypto.com.
- Lazarus stole a record $1.7 billion in crypto in 2022, according to Chainalysis. That’s more than 12 times the $142m of exports that North Korea managed in 2020.
2023
- April 6 — DL News reported how the Lazarus Group’s activities help to accelerate North Korea’s nuclear programme, bolstered by the nation’s so-called Treasure Sword — stolen crypto. “All the money [the North Korean hackers] cash out goes to fund their missile programme,” said Erin Plante at Chainalysis.
- June 3 — Non-custodial crypto wallet Atomic announced that user wallets may be compromised, following multiple reports of user accounts being drained. Nearly $100 million was stolen. Analytics firm Elliptic attributed the attack to Lazarus.
- July 23 — Lazarus hacks centralised crypto payment provider Alphapo for nearly $60 million.
- August 22 — The FBI said Lazarus was preparing to offload $41 million in stolen crypto mixed from several heists.
- September 4 — Stake.com was breached by a suspected hot wallet key leak, and $41 million in crypto was moved off the platform. Days later, the FBI attributed the hack to Lazarus.
- September 12 — Crypto exchange CoinEx was hacked.
- September 13 — Crypto twitter sleuth ZachXBT raised the possibility that Lazarus was behind the CoinEx hack. Blockchain research firm SlowMist verified ZachXBT’s claim. The stolen amount was eventually calculated to reach about $54 million.
Tyler Pearson is a researcher at DL News. He is based out of Alberta, Canada. Got a tip? Reach out to him at ty@dlnews.com.